
Medusa Ransomware
Configurable, Flexible, and Relentless
In the crowded ransomware ecosystem, most families carve out their niche with speed, stealth, or sheer brutality. Medusa, however, distinguishes itself through adaptability. Unlike its rivals that follow rigid playbooks, Medusa behaves more like a ransomware toolkit one that operators can fine-tune to match the victim, the environment, and even the attacker’s preference.
This configurability isn’t theoretical; it’s built directly into the malware. From choosing whether to encrypt an entire system or just a single directory, to selectively sparing system drives so the ransom note remains visible, Medusa provides operators with an unusual level of control. The result is a ransomware family that can be loud or quiet, surgical or indiscriminate depending entirely on the attacker’s goal.
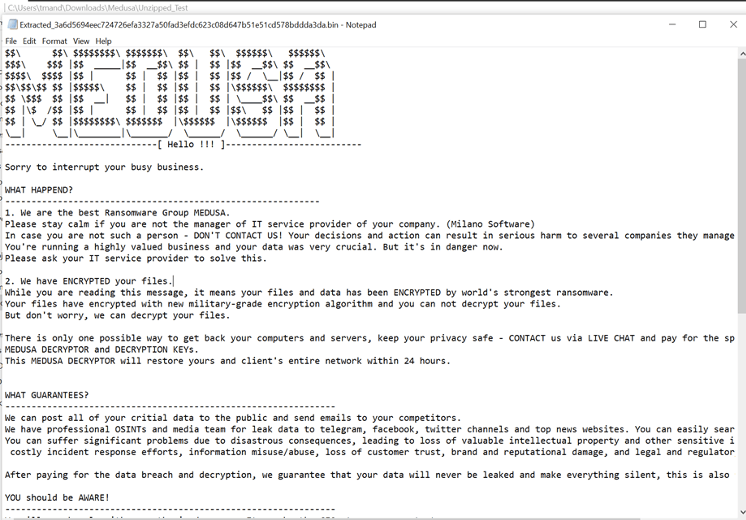
Medusa first appeared in the wild in 2021 but has steadily evolved into a high-impact threat that combines classic file encryption with modern double-extortion tactics. Its leak sites and Telegram channels amplify pressure on victims, ensuring that the threat doesn’t end with locked files stolen data can also be weaponized for public shaming and reputational damage.
What makes Medusa dangerous isn’t just its encryption routines, but its operational flexibility. In the hands of affiliates, it becomes a shapeshifter capable of behaving like a blunt hammer in one campaign and a scalpel in the next. For defenders, this variability makes Medusa particularly difficult to model, detect, and contain.
Technical Overview of Medusa
Medusa doesn’t hide behind layers of obfuscation or elaborate loaders. Its binaries often look unassuming at first glance, but what sets it apart is the control it hands to the operator. Where most ransomware families follow rigid, predefined paths, Medusa behaves like a toolkit, configurable at runtime to match the attacker’s intent.
Execution with Options
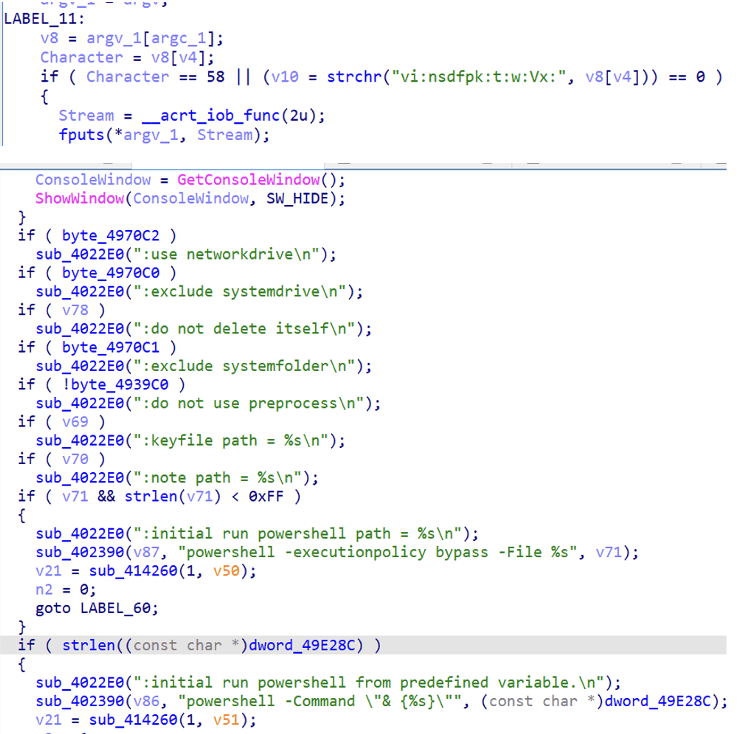
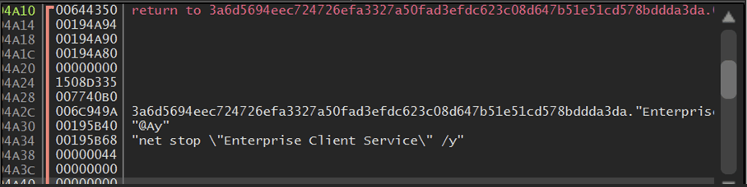
At the heart of Medusa is a flexible command-line interface. Affiliates can choose how the ransomware behaves by passing in a set of flags that control visibility, scope, and even cleanup. Want the malware to encrypt a single directory while leaving the rest of the system untouched? Use the -i flag. Need to extend damage across mapped network drives? Pass -n. Want the OS to keep running so the ransom note can be read? Exclude the system drive with -s.
Even its presence on the machine is negotiable. By default, Medusa erases itself at the end of execution, using a timed self-deletion command (cmd /c ping localhost -n 3 > nul & del %s) to minimize forensic traces. But if the attacker prefers to keep the binary for debugging or persistence, a single flag disables that feature.
This menu of execution paths means the same Medusa sample can cause a full-scale outage in one incident and a carefully scoped disruption in another. Flexibility, not flashiness, is its defining strength.
Operators can decide whether to:
- Run the ransomware in visible or silent mode (-v).
Encrypt a single directory (-i <path>) or the entire system by default. - Extend impact to network drives (-n).
- Spare the main system drive (-s) or system folders (-f) to keep the OS functional long enough to display ransom notes.
- Skip preprocessing like service termination or shadow copy deletion (-p).
- Provide external encryption keys (-k) or ransom note files (-t).
- Execute custom PowerShell scripts during runtime (-w).
Evasion and Fingerprinting
Before it touches a single file, Medusa clears the battlefield. The ransomware systematically terminates services and processes that might interfere with encryption, focusing heavily on backup, security, and database software.
Targets include:
- Backup and disaster recovery tools (Veeam, Acronis,
- Symantec System Recovery).
Security products (Sophos, McAfee, Malwarebytes, Endpoint Protection agents). - Database services (SQLsafe, Microsoft SQL, and others).
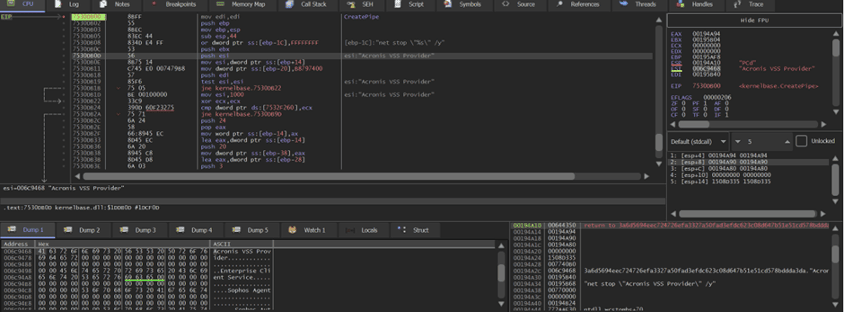
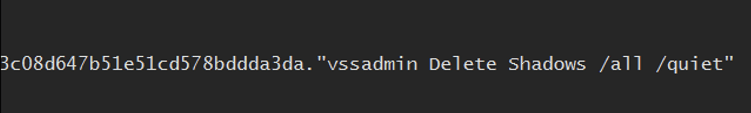
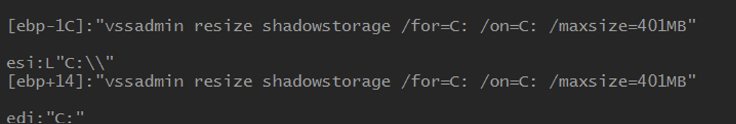
To further weaken recovery options, Medusa also attacks Windows Volume Shadow Copies. It not only deletes them outright using commands such as vssadmin Delete Shadows /all /quiet, but also resizes shadow storage so that any surviving snapshots are rendered unusable.
By disabling these, Medusa ensures files are unlocked and that recovery paths are crippled. This ruthless preparation dramatically increases the success rate of its encryption stage.
Though Medusa lacks the heavy packing and obfuscation of more modern ransomware families, it does carry selective defenses that make analysis and detection more challenging. One standout feature is its use of the GetSystemFirmwareTable API, a low-level system call rarely seen outside hardware diagnostic tools. Medusa leverages this to pull firmware data and check for virtualization artifacts, helping it avoid automated sandbox environments.
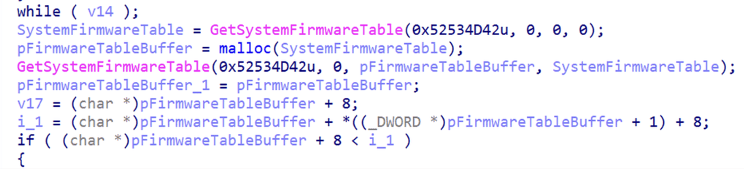
At the same time, the same fingerprinting process doubles as a way to generate unique victim identifiers, binding each ransom case to the physical machine it infected. This approach reinforces Medusa’s identity as ransomware designed for adaptability: it doesn’t need a complex loader when it can quietly profile, evade, and individualize each infection from within its own codebase.
Keys, Notes, and Fallbacks
Encryption keys and ransom notes are the backbone of any ransomware operation, and Medusa handles them with equal parts rigor and resilience. If provided by the operator, external RSA key files are validated down to the byte (exactly 450 bytes in size) before use. Likewise, custom ransom notes can be supplied at runtime and injected directly into memory.
But Medusa never assumes perfect setup. If no external key or note is present, it simply pivots to its built-in resources. Medusa’s encryption engine is built on the Windows BCrypt library, a reliable cryptographic foundation. Analysis shows:
- Hybrid cryptography: RSA public keys secure per-file AES session keys.
- Hardcoded IVs: Initialization vectors are directly embedded in the executable and loaded into memory.
- Targeted exclusions: System folders and OS-critical paths are skipped to avoid rendering systems unbootable.
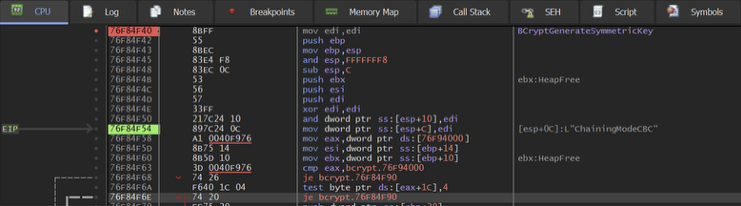
This design balances operational reliability (victims can still access ransom notes and negotiate) with cryptographic irreversibility (recovery without the attackers’ keys is practically impossible).
The notes themselves are concise but multi-channeled. Victims are typically directed to TOX IDs, Tor-based portals, and Telegram channels, ensuring that communications remain anonymous and resilient even if one channel is taken down.
This dual approach operator-supplied or fallback ensures Medusa never fails gracefully. It will always encrypt. It will always leave instructions.
MITRE ATT&CK Mapping for Medusa
| Tactic | Technique | ID | Details |
|---|---|---|---|
| Initial Access | User Execution: Malicious File | T1204.002 | Delivered as executables that require a victim or attacker to trigger. |
| Execution | Command and Scripting Interpreter | T1059 | Controlled via command-line arguments; can invoke custom PowerShell scripts. |
| Privilege Escalation | Abuse Elevation Control Mechanism | T1548 | Requires elevated rights to terminate services and access protected files. |
| Defense Evasion | Impair Defenses: Disable Security Tools | T1562.001 | Terminates AV, EDR, and backup processes (e.g., Sophos, McAfee, Veeam). |
| Defense Evasion | Virtualization / Sandbox Evasion | T1497 | Uses GetSystemFirmwareTable for VM and sandbox detection. |
| Discovery | System Information Discovery | T1082 | Gathers hardware details, used for fingerprinting and victim IDs. |
| Discovery | File and Directory Discovery | T1083 | Enumerates logical drives and targeted directories for encryption. |
| Impact | Data Encrypted for Impact | T1486 | Encrypts files with BCrypt libraries; uses AES/RSA hybrid approach. |
| Impact | Inhibit System Recovery | T1490 | Disables backups and recovery tools to maximize impact. |
Indicators of Compromise (IOCs)
Analysis of Medusa ransomware campaigns reveals a set of recurring artifacts across binaries, system behavior, and network infrastructure. These indicators can assist defenders in detection, hunting, and incident response.
File Hashes (SHA-256)
- 3a6d5694eec724726efa3327a50fad3efdc623c08d647b51e51cd578bddda3da
- 0065b818525d8a364f5d9e4b801e3408dad6576ce6d8ca5c01b19c3857a08d64
- 0382f4930cb892b43c80ef147ad617c332a7c2e298502ef0e6663b2b48319460
- 08b74bb2d6ec9bbdabdd92fb32d8322d2e08b45b0be069c7429675d33d5060c7
- 19b65ef538144e873271f547807830a5ba31fe215f2fe7ade51a38047a80834b
- 33ef66ec811267739a975c776b75787e819a26761e232f0b3eb4b32e7ef560d8
- 3a6d5694eec724726efa3327a50fad3efdc623c08d647b51e51cd578bddda3da
- 3d091b32abd008ff392158ff4d7271f72febe6069b4b1b3ccd51a2a733e37327
- 49916c9c2a9d6b3c60f541891966bfff62e9b3eb9b682ced8600e7e9415b033d
- 4a0e7565db16ed833a083bc9927f032be5e6918eed712982cd76e87e99510778
- 94f420e16a4eb5154076895cd8c5f677db4273d37d44b81e1d04b26e851b69fe
- 9ec6bf1ad038e6c7f5bf9be374d3299df033424ef1399a8ffd892df40efd6353
- a0cebcc9f5893b2fde2806794c27b8a304a0eb863e128ad779ed5dd806ad9239
- bcd952d2995d187c5a87ec0e03b638e02d7157b9a01d4e7c28ce7a6d6b28ac42
- c9abfc3e4da474e18795f5261f77e60c44e7b3353771281e4304e7506d56fdb4
- df0f05469702bd70c49045dcbbefc65e735f4116bdb12526cd16110472a51dc8
File Artifacts
- Encrypted File Extensions: Often appended with Medusa-specific markers (.MEDUSA).
- Ransom Note: Custom or embedded notes, typically dropped across directories(!!!READ_ME_MEDUSA!!!.txt).
- Execution Flags: Presence of unusual command-line arguments (-i, -n, -s, -k, -t, -w).
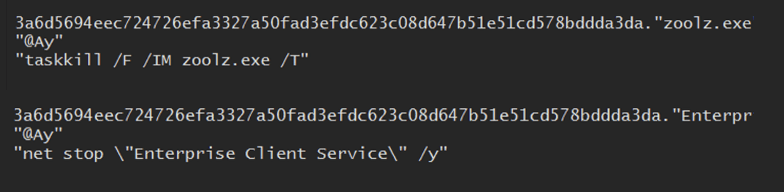
- Self-Deletion Routine: cmd /c ping localhost -n 3 > nul & del %s.
Process & Service Termination
Medusa systematically stops processes tied to backups, EDR, and databases, including:
- Veeam Backup Catalog Data Service
- Acronis VSS Provider
- Symantec System Recovery
- Sophos Agent / McAfee Framework / Malwarebytes Services
- SQLsafe Backup / SQLsafe Filter Service
Cryptographic Material
- RSA public key (450-byte validated input or embedded, obfuscated block).
- AES session keys generated per file using BCrypt APIs.
- Hardcoded IVs observed in some samples.
Network Indicators
- Tor Leak Sites: Used for data dumps and victim shaming.
(http://xfv4jzckytb4g3ckwemcny3ihv4i5p4lqzdpi624cxisu35my5fwi5qd[dot]onion/)
(http://7aqabivkwmpvjkyefonf3gpy5gsubopqni7kcirsrq3pflckxq5zz4id[dot]onion/) - TOX IDs: Frequently embedded in ransom notes for negotiation.
- Telegram Channels: Backup communication infrastructure.
(Exact addresses vary by campaign and are often rotated.)
Defensive Takeaways: Staying Ahead of Medusa
By the time Medusa begins encrypting files, the window for response is already closing. Defenders need to focus on detecting the precursor behaviors that signal an attack in motion and hardening systems against the services and processes Medusa routinely disrupts.
- Monitor Service Termination
Medusa aggressively halts security, backup, and database processes to free files for encryption. Monitoring for bulk net stop commands or suspicious termination of services like Veeam, Sophos, McAfee, SQLsafe, and Acronis can serve as an early warning.
- Watch for Command-Line Abuses
Unusual use of execution flags (-i, -n, -s, -k, -t) or PowerShell invocations tied to encryption routines should raise red flags. These patterns are rarely seen in legitimate enterprise workflows. - Detect Rare API Calls
The use of GetSystemFirmwareTable is highly unusual outside hardware diagnostics. Flagging this API call can help identify sandbox-evasion attempts linked to Medusa. - Harden Recovery Paths
Since Medusa targets backups directly, organizations should maintain offline and immutable backups. Regular testing of recovery procedures is just as critical as maintaining the backups themselves.
- Limit Privileges and Segment Networks
Medusa’s ability to stop system services and encrypt broadly depends on elevated rights and lateral movement. Enforcing least privilege access and strong network segmentation reduces its blast radius.
Final Thoughts
Medusa is not the flashiest ransomware family on the scene. It doesn’t lean on zero-days, novel cryptography, or extreme stealth. Instead, its strength lies in adaptability. Every flag, every runtime choice, turns it into a slightly different weapon capable of quiet precision or widescale disruption, depending on the operator’s intent.
That flexibility makes Medusa one of the more unpredictable threats facing defenders today. Unlike families locked into a single modus operandi, Medusa can be tuned to fit the environment it’s attacking, from a targeted hit on a single server to a full network takedown. Combined with double extortion and an active leak ecosystem, it remains a serious and evolving threat.
For defenders, the lesson is clear: don’t just hunt for encryption events hunt for the precursors. Mass service stoppages, suspicious command-line arguments, or rare API calls like GetSystemFirmwareTable are signs that Medusa is setting the stage. By disrupting it early, organizations can avoid being trapped in its extortion cycle.
