
In a threat landscape already teeming with complex malware families, one might expect the next big name in ransomware to come wrapped in layers of obfuscation, zero-day exploits, and bleeding-edge evasion tactics. Instead, what emerged in early 2025 was something entirely different: something faster, leaner, and disturbingly effective.
Bert ransomware doesn’t try to be stealthy. It doesn’t hide behind advanced packing or polymorphism. It simply does its job encrypting data across Windows and Linux systems with clinical precision and then vanishes, leaving chaos in its wake.
Early sightings place its victims in Asia and Europe, with a growing footprint in the United States. The targets? Organizations where downtime hurts the most: healthcare providers, software vendors, and logistics firms, all hit with a level of disruption that feels both intentional and deeply rehearsed. What sets Bert apart isn’t its complexity, but its efficiency. On Windows, it leans on native .NET tools and multithreaded routines to encrypt data rapidly. On Linux, it scales even harder, leveraging dozens of threads and even forcibly shutting down virtual machines to ensure maximum reach. In either environment, its purpose is clear: act quickly, leave a mess, and offer victims a single, stark option:
pay
But despite its blunt nature, Bert is far from careless. If anything, it’s deliberate.
For instance, its Windows variant uses a PowerShell loader that disables Windows Defender, alters firewall rules, and suppresses User Account Control before quietly pulling the main payload from attacker infrastructure hosted in Sweden but linked to Russian control. Once deployed, the ransomware executes with admin privileges and begins its work almost immediately.
.jpeg)
.jpeg)
The executable itself is a C# console application compiled for 64-bit systems and built on the .NET CLR. Decompilation reveals a reliance on familiar namespaces: System.IO, System. Security. Cryptography, System. Diagnostics. This isn’t some experimental or cobbled-together malware; it’s structured, readable, and clearly built for rapid deployment across enterprise environments.
Before encrypting anything, Bert clears the path. It searches for backend processes and terminates them not selectively, but systematically. Services tied to SQL, MongoDB, Docker, Java apps, and web servers are all in the crosshairs. The ransomware has an internal list of keywords and cycles through running processes using standard .NET APIs. Anything that matches is killed on the spot.
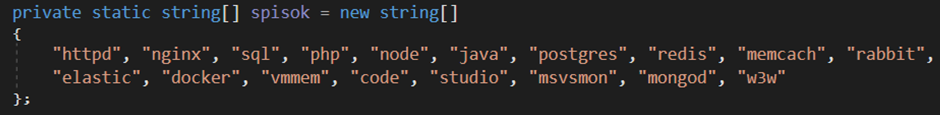
Interestingly, the kill logic is wrapped in a try-catch block. Why? Because failure isn’t a deal-breaker. If permissions don’t allow termination, Bert simply moves on. This silent resilience makes it extremely difficult to interrupt once it begins its routine.
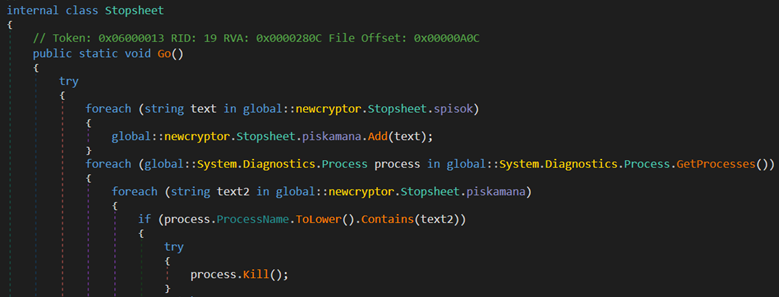
The rationale is ruthlessly practical: eliminate file locks. By terminating database services and applications, Bert ensures that critical files are not held open, preventing errors and maximizing the number of files it can successfully encrypt. In doing so, Bert sidesteps many of the pitfalls that slow other ransomware families down, like locked files or inaccessible volumes.
With the deck cleared, Bert begins enumerating all mounted logical drives. It scans every directory recursively, building out per-drive file lists and preparing the ransom note, note.txt, which it drops into every folder it touches.
But it doesn’t encrypt blindly. System directories are skipped. Files inside C:\Windows are ignored. So are executables, drivers, shortcuts, and the ransom note itself. There’s no appetite for crashing the system or locking itself out of its own message.
.png)
It’s a surgical approach one designed not to destroy, but to cripple just enough that paying the ransom becomes the path of least resistance.
The actual encryption logic reflects the same attention to speed and control. Bert uses AES encryption per file, generating a unique key and Initialization Vector (IV) for each target.
But there’s a twist that prioritizes speed: intermittent encryption. The result is a file that becomes completely unusable to the victim but is encrypted in a fraction of the time.
.png)
All encryption is handled in parallel. Each drive spawns its own threads, which work through file lists in a staggered, round-robin style to avoid bottlenecks. A shared counter tracks completion, ensuring the program exits cleanly after all jobs are done. This multithreaded model makes the ransomware extremely fast, especially on multi-core systems, and significantly reduces the window defenders have to respond once execution begins.
The ransom note itself is short and to the point. Files have been encrypted, data may have been exfiltrated, and recovery hinges on contacting the attackers via Session, a privacy-focused messaging app designed to evade surveillance and takedowns.
.png)
Victims are given a Session ID and a Tor-based blog address to begin negotiations. No email, no traditional chat portal just encrypted, anonymous communications over decentralized infrastructure. It’s a growing trend among ransomware operators, and Bert is clearly aligned with that shift.
Digging into the internals of the Bert ransomware sample reveals a number of subtle but telling technical choices. This isn’t bloated or overengineered malware; it’s precise and purposeful.
The payload, newcryptor.exe, is a .NET 64-bit console application written in C#, compiled with modern compiler security features like DEP and ASLR enabled. Here’s what stood out:
017f565ff07e48364f6d1da0c2ef3f66110b043b38aea6b66f282afa5b803a31
25c693808095f45d297171eba5196e9a5176281a2d248cb1a8cfa07a68bbe332
5bba035c4cb3c2e09a355d9356b3397184af4bf1ac1ff1df99ae9c15edee9f2b
6182df9c60f9069094fb353c4b3294d13130a71f3e677566267d4419f281ef02
78eb838238dad971dcbc46b86491d95e297f3d47dc770de5c43af3163990d31c
7b5efacb6a1e7d735f5342f69f0d27868bc088d14ee7552014e266160f50a908
8478d5f5a33850457abc89a99718fc871b80a8fb0f5b509ac1102f441189a311
c7efe9b84b8f48b71248d40143e759e6fc9c6b7177224eb69e0816cc2db393db
ced4ed5e5ef7505dd008ed7dd28b8aff38df7febe073d990d6d74837408ea4be
f2dc218ea8e2caa8668e54bae6561afd9fbf035a40b80ce9e847664ff0809799
Given Bert's focus on speed, prevention and early detection are paramount. Standard defenses may be too slow to react once the encryption process begins.
Bert is not an innovation showcase. It’s not a zero-day exploit kit or a nation-state-level implant. But it’s effective brutally so.
What makes Bert dangerous isn’t its complexity. It’s the discipline behind it. Every design choice serves the goal of speed, stability, and maximum impact. It doesn’t overreach. It doesn’t crash systems. It doesn’t even encrypt everything just enough to force a decision.
As ransomware continues to evolve, threats like Bert are a reminder that the most effective tools aren’t always the most advanced. Sometimes, it’s the ones built by experienced hands, using standard APIs, executed with precision.
For defenders, the takeaway is clear: modern ransomware doesn’t need to be stealthy if it’s fast enough. Early detection, proactive kill chain disruption, and real-time endpoint monitoring remain critical. Because once Bert starts encrypting, the clock’s already run out.